1. What is the projected Compound Annual Growth Rate (CAGR) of the Ultra Secure Endpoint?
The projected CAGR is approximately XX%.
MR Forecast provides premium market intelligence on deep technologies that can cause a high level of disruption in the market within the next few years. When it comes to doing market viability analyses for technologies at very early phases of development, MR Forecast is second to none. What sets us apart is our set of market estimates based on secondary research data, which in turn gets validated through primary research by key companies in the target market and other stakeholders. It only covers technologies pertaining to Healthcare, IT, big data analysis, block chain technology, Artificial Intelligence (AI), Machine Learning (ML), Internet of Things (IoT), Energy & Power, Automobile, Agriculture, Electronics, Chemical & Materials, Machinery & Equipment's, Consumer Goods, and many others at MR Forecast. Market: The market section introduces the industry to readers, including an overview, business dynamics, competitive benchmarking, and firms' profiles. This enables readers to make decisions on market entry, expansion, and exit in certain nations, regions, or worldwide. Application: We give painstaking attention to the study of every product and technology, along with its use case and user categories, under our research solutions. From here on, the process delivers accurate market estimates and forecasts apart from the best and most meaningful insights.
Products generically come under this phrase and may imply any number of goods, components, materials, technology, or any combination thereof. Any business that wants to push an innovative agenda needs data on product definitions, pricing analysis, benchmarking and roadmaps on technology, demand analysis, and patents. Our research papers contain all that and much more in a depth that makes them incredibly actionable. Products broadly encompass a wide range of goods, components, materials, technologies, or any combination thereof. For businesses aiming to advance an innovative agenda, access to comprehensive data on product definitions, pricing analysis, benchmarking, technological roadmaps, demand analysis, and patents is essential. Our research papers provide in-depth insights into these areas and more, equipping organizations with actionable information that can drive strategic decision-making and enhance competitive positioning in the market.
 Ultra Secure Endpoint
Ultra Secure EndpointUltra Secure Endpoint by Type (Android System, Other Systems, World Ultra Secure Endpoint Production ), by Application (Governmental Agencies, Military & Defense, Aerospace, Business, Other), by North America (United States, Canada, Mexico), by South America (Brazil, Argentina, Rest of South America), by Europe (United Kingdom, Germany, France, Italy, Spain, Russia, Benelux, Nordics, Rest of Europe), by Middle East & Africa (Turkey, Israel, GCC, North Africa, South Africa, Rest of Middle East & Africa), by Asia Pacific (China, India, Japan, South Korea, ASEAN, Oceania, Rest of Asia Pacific) Forecast 2025-2033
The ultra-secure endpoint market is experiencing robust growth, driven by escalating cyber threats and increasing regulatory compliance mandates across diverse sectors. The market, estimated at $5 billion in 2025, is projected to exhibit a Compound Annual Growth Rate (CAGR) of 15% from 2025 to 2033, reaching approximately $15 billion by 2033. This expansion is fueled by the rising adoption of remote work models, the proliferation of Internet of Things (IoT) devices, and the growing sophistication of cyberattacks targeting sensitive data. Key market drivers include the need for enhanced data protection, improved network security, and robust endpoint device management capabilities. Government and financial institutions are leading the adoption, followed by healthcare and other data-sensitive industries. The market is segmented by endpoint type (laptops, desktops, mobile devices, IoT), security features (encryption, access control, threat detection), and deployment model (cloud, on-premise). Competitive landscape is characterized by both established players like BlackBerry and Atos, and specialized niche providers such as X-Systems and Silent Circle, each offering unique solutions tailored to specific security needs.
Continued innovation in areas like AI-powered threat detection, advanced encryption technologies, and zero-trust architectures are shaping the future trajectory of the ultra-secure endpoint market. However, challenges remain, including the high cost of implementation and maintenance of these sophisticated solutions, and the complexity associated with integrating them into existing IT infrastructures. Furthermore, the ever-evolving nature of cyber threats requires continuous updates and adaptations to maintain effective security postures. Despite these constraints, the increasing awareness of the risks associated with data breaches and the stringent regulatory landscape will continue to fuel market expansion in the years to come, creating opportunities for both established and emerging players in the ultra-secure endpoint space.
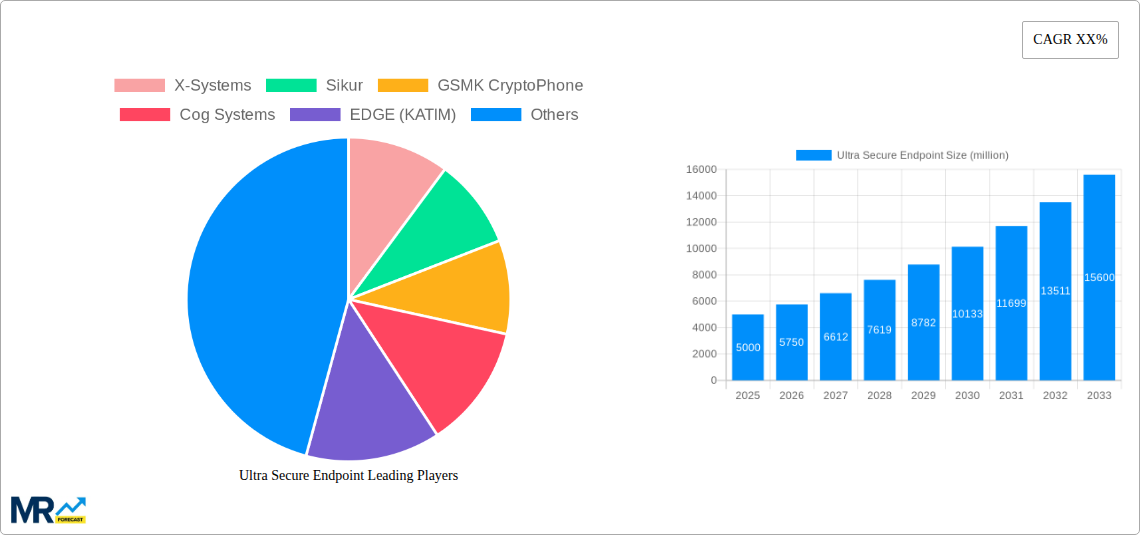
The ultra-secure endpoint market is experiencing explosive growth, driven by escalating cyber threats and the increasing reliance on remote work and mobile devices. Over the study period (2019-2033), we project the market will witness a significant expansion, exceeding several million units in sales by 2033. The estimated market value for 2025 surpasses several million USD, reflecting the growing demand for robust security solutions across various sectors. This surge isn't just about preventing data breaches; it's about maintaining operational continuity, protecting sensitive intellectual property, and ensuring regulatory compliance. The historical period (2019-2024) saw a steady rise in adoption, particularly amongst government agencies, financial institutions, and healthcare providers, all grappling with increasingly sophisticated and persistent attacks. However, the forecast period (2025-2033) promises even more dramatic growth fueled by the increasing adoption of cloud-based solutions, the expansion of the Internet of Things (IoT), and the growing awareness of the vulnerabilities inherent in traditional endpoint security measures. The base year for our analysis is 2025, providing a crucial benchmark against which to measure future market trajectories. This trend is further amplified by the increasing sophistication of cyberattacks, necessitating solutions beyond basic antivirus and firewall protection. The demand for advanced encryption, secure boot processes, and tamper-evident hardware is driving innovation and market expansion. The market's evolution shows a clear shift toward holistic security approaches that integrate endpoint protection with wider network and data security strategies. This integrated approach is crucial in addressing the complexities of modern cyber threats, which often involve multiple attack vectors. The rising adoption of Artificial Intelligence (AI) and Machine Learning (ML) in endpoint security is further enhancing the effectiveness of these solutions, allowing for real-time threat detection and automated response.
Several factors are propelling the growth of the ultra-secure endpoint market. The increasing frequency and severity of cyberattacks targeting endpoints are a primary driver. Organizations are realizing that traditional security measures are insufficient to combat sophisticated threats like ransomware, advanced persistent threats (APTs), and zero-day exploits. The shift towards remote work, accelerated by recent global events, has significantly expanded the attack surface, making endpoints more vulnerable. Governments worldwide are increasingly enacting stringent data privacy regulations (like GDPR and CCPA), requiring organizations to adopt robust endpoint security measures to ensure compliance. This regulatory pressure is pushing companies to invest heavily in ultra-secure solutions to avoid hefty fines and reputational damage. Furthermore, the rising adoption of cloud-based services and the expansion of the Internet of Things (IoT) are creating new vulnerabilities that need to be addressed. Ultra-secure endpoints, with their advanced encryption and secure boot processes, are essential for protecting data both in transit and at rest in these increasingly interconnected environments. The increasing adoption of bring-your-own-device (BYOD) policies also adds to the complexity and necessitates a robust ultra-secure endpoint strategy. This necessitates a shift away from traditional, perimeter-based security models toward more comprehensive and integrated security approaches that protect all endpoints regardless of location or access method.
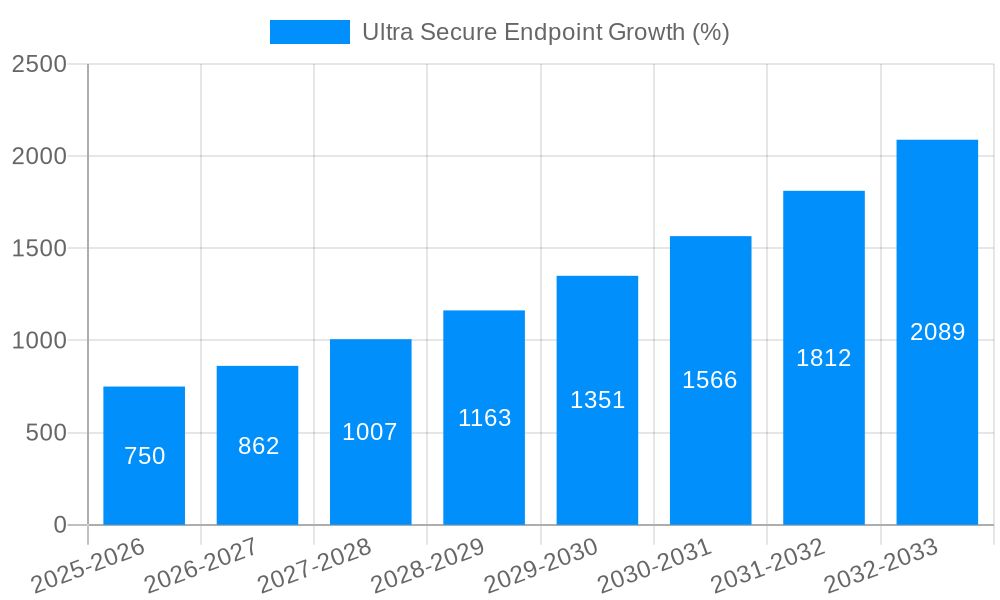
Despite the significant growth potential, the ultra-secure endpoint market faces several challenges. The high cost of implementation is a major barrier for small and medium-sized enterprises (SMEs), which may lack the resources to invest in advanced security solutions. The complexity of deploying and managing these solutions also presents a significant hurdle. Specialized expertise is often required for proper configuration and maintenance, increasing operational costs and potentially creating a skills gap within organizations. Furthermore, the constant evolution of cyber threats requires ongoing updates and upgrades to maintain effectiveness, leading to a continuous cycle of investment and maintenance. Interoperability issues between different ultra-secure endpoint solutions can also create complications for organizations with diverse IT infrastructures. Ensuring seamless integration with existing systems and avoiding vendor lock-in are crucial considerations. Finally, user experience can be a factor, as some ultra-secure solutions may impose limitations on functionality or usability that impact employee productivity. Finding a balance between robust security and user-friendliness is a key challenge for vendors in this market.
The ultra-secure endpoint market is expected to witness substantial growth across various regions and segments.
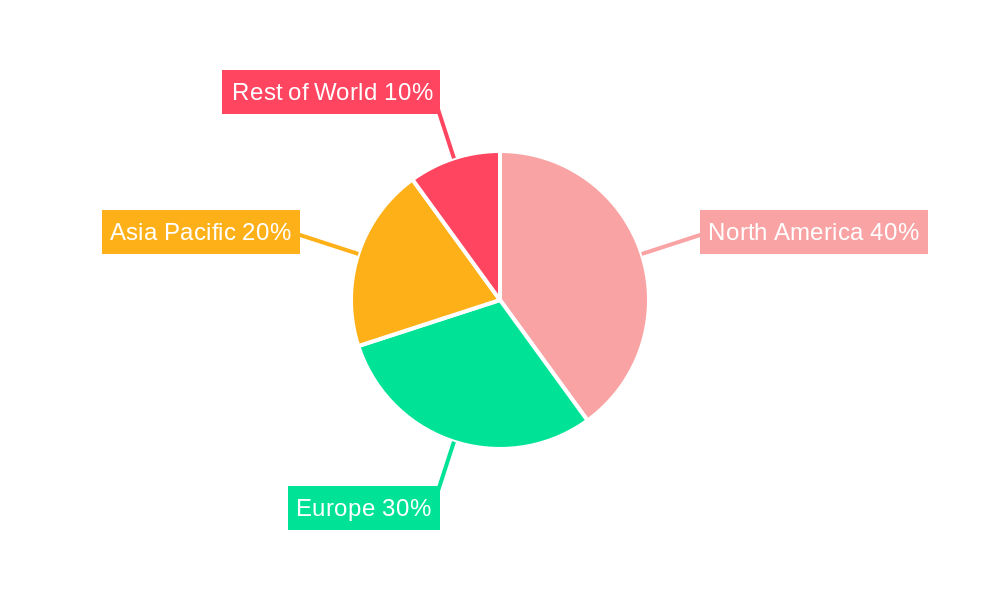
North America: This region is projected to hold a significant market share due to the high adoption of advanced security technologies, strong regulatory compliance requirements, and the presence of major technology companies. The well-established IT infrastructure and the high concentration of financial institutions and government agencies contribute to the region's dominance.
Europe: Driven by strict data protection regulations (like GDPR), Europe is experiencing strong growth in the ultra-secure endpoint market. The focus on privacy and data security is driving demand for advanced solutions among businesses and government entities.
Asia-Pacific: This region is experiencing rapid growth due to increasing digitalization, rising cybersecurity awareness, and economic expansion in several key countries. The adoption of ultra-secure endpoints is being driven by both the private and public sectors.
Key Segments:
Government and Defense: This segment is a significant driver of market growth due to the critical need to protect sensitive data and national infrastructure. The demand for highly secure endpoints is particularly strong in this sector.
Financial Services: Financial institutions are increasingly adopting ultra-secure endpoints to protect against fraud, data breaches, and regulatory non-compliance. The high value of financial data makes this sector a prime target for cyberattacks.
Healthcare: The healthcare industry is becoming increasingly reliant on digital technologies, creating a need for robust endpoint security to protect sensitive patient data and comply with regulations such as HIPAA. The potential for severe consequences from data breaches fuels investment in this area.
In summary, the convergence of increasing cyber threats, stringent regulations, and the expanding digital landscape creates a compelling case for the sustained growth of ultra-secure endpoint solutions across these key regions and segments. The market is expected to see significant expansion driven by the increasing awareness of vulnerabilities and the need for sophisticated security measures. North America, initially leading due to strong established technology sectors and regulations, is expected to maintain its strong position. However, the Asia-Pacific region and Europe, driven by stringent regulations and robust digital adoption, will witness considerable growth in the forecast period.
Several factors contribute to the projected growth of the ultra-secure endpoint market. The increasing sophistication of cyberattacks and the growing awareness of data breaches are driving demand for more robust security measures. Government regulations aimed at improving data privacy are further boosting the market, while the rising adoption of cloud-based services and the Internet of Things (IoT) are expanding the attack surface, necessitating advanced endpoint protection. The integration of AI and machine learning into these solutions is enhancing their effectiveness and further fueling market expansion.
This report provides a comprehensive overview of the ultra-secure endpoint market, analyzing current trends, driving forces, challenges, and growth catalysts. It offers detailed insights into key market segments and regions, identifying the leading players and significant developments shaping the industry's future. The report also provides detailed market forecasts for the period 2025-2033, offering valuable insights for businesses and stakeholders operating within this dynamic sector. This information is crucial for strategic decision-making and investment planning.
| Aspects | Details |
|---|---|
| Study Period | 2019-2033 |
| Base Year | 2024 |
| Estimated Year | 2025 |
| Forecast Period | 2025-2033 |
| Historical Period | 2019-2024 |
| Growth Rate | CAGR of XX% from 2019-2033 |
| Segmentation |
|




Note*: In applicable scenarios
Primary Research
Secondary Research

Involves using different sources of information in order to increase the validity of a study
These sources are likely to be stakeholders in a program - participants, other researchers, program staff, other community members, and so on.
Then we put all data in single framework & apply various statistical tools to find out the dynamic on the market.
During the analysis stage, feedback from the stakeholder groups would be compared to determine areas of agreement as well as areas of divergence
The projected CAGR is approximately XX%.
Key companies in the market include X-Systems, Sikur, GSMK CryptoPhone, Cog Systems, EDGE (KATIM), Atos, Bittium, Silent Circle, BlackBerry, Purism.
The market segments include Type, Application.
The market size is estimated to be USD XXX million as of 2022.
N/A
N/A
N/A
N/A
Pricing options include single-user, multi-user, and enterprise licenses priced at USD 4480.00, USD 6720.00, and USD 8960.00 respectively.
The market size is provided in terms of value, measured in million and volume, measured in K.
Yes, the market keyword associated with the report is "Ultra Secure Endpoint," which aids in identifying and referencing the specific market segment covered.
The pricing options vary based on user requirements and access needs. Individual users may opt for single-user licenses, while businesses requiring broader access may choose multi-user or enterprise licenses for cost-effective access to the report.
While the report offers comprehensive insights, it's advisable to review the specific contents or supplementary materials provided to ascertain if additional resources or data are available.
To stay informed about further developments, trends, and reports in the Ultra Secure Endpoint, consider subscribing to industry newsletters, following relevant companies and organizations, or regularly checking reputable industry news sources and publications.