1. What is the projected Compound Annual Growth Rate (CAGR) of the Mobile Data Security Tool?
The projected CAGR is approximately XX%.
MR Forecast provides premium market intelligence on deep technologies that can cause a high level of disruption in the market within the next few years. When it comes to doing market viability analyses for technologies at very early phases of development, MR Forecast is second to none. What sets us apart is our set of market estimates based on secondary research data, which in turn gets validated through primary research by key companies in the target market and other stakeholders. It only covers technologies pertaining to Healthcare, IT, big data analysis, block chain technology, Artificial Intelligence (AI), Machine Learning (ML), Internet of Things (IoT), Energy & Power, Automobile, Agriculture, Electronics, Chemical & Materials, Machinery & Equipment's, Consumer Goods, and many others at MR Forecast. Market: The market section introduces the industry to readers, including an overview, business dynamics, competitive benchmarking, and firms' profiles. This enables readers to make decisions on market entry, expansion, and exit in certain nations, regions, or worldwide. Application: We give painstaking attention to the study of every product and technology, along with its use case and user categories, under our research solutions. From here on, the process delivers accurate market estimates and forecasts apart from the best and most meaningful insights.
Products generically come under this phrase and may imply any number of goods, components, materials, technology, or any combination thereof. Any business that wants to push an innovative agenda needs data on product definitions, pricing analysis, benchmarking and roadmaps on technology, demand analysis, and patents. Our research papers contain all that and much more in a depth that makes them incredibly actionable. Products broadly encompass a wide range of goods, components, materials, technologies, or any combination thereof. For businesses aiming to advance an innovative agenda, access to comprehensive data on product definitions, pricing analysis, benchmarking, technological roadmaps, demand analysis, and patents is essential. Our research papers provide in-depth insights into these areas and more, equipping organizations with actionable information that can drive strategic decision-making and enhance competitive positioning in the market.
 Mobile Data Security Tool
Mobile Data Security ToolMobile Data Security Tool by Type (Cloud-based, On-premises), by Application (SMEs, Large Enterprises), by North America (United States, Canada, Mexico), by South America (Brazil, Argentina, Rest of South America), by Europe (United Kingdom, Germany, France, Italy, Spain, Russia, Benelux, Nordics, Rest of Europe), by Middle East & Africa (Turkey, Israel, GCC, North Africa, South Africa, Rest of Middle East & Africa), by Asia Pacific (China, India, Japan, South Korea, ASEAN, Oceania, Rest of Asia Pacific) Forecast 2026-2034
The mobile data security tool market is experiencing robust growth, driven by the increasing reliance on mobile devices for both personal and professional use, coupled with the escalating number of cyber threats targeting mobile platforms. The market, estimated at $15 billion in 2025, is projected to expand at a Compound Annual Growth Rate (CAGR) of 15% from 2025 to 2033, reaching an estimated value of $50 billion by 2033. This expansion is fueled by several key factors, including the rising adoption of cloud-based security solutions offering enhanced scalability and flexibility, the growing need for robust data protection amongst Small and Medium-sized Enterprises (SMEs) and large enterprises, and the increasing sophistication of mobile malware and data breaches. The market is segmented by deployment type (cloud-based and on-premises) and by user type (SMEs and large enterprises), with cloud-based solutions gaining significant traction due to their cost-effectiveness and ease of management. Geographical expansion is also a significant driver, with North America and Europe currently holding the largest market shares, but significant growth potential is anticipated in the Asia-Pacific region driven by increasing smartphone penetration and rising digital literacy.


Despite the positive growth trajectory, the market faces certain restraints. These include the high cost of implementation for advanced security solutions, particularly for SMEs, the complexity of managing diverse mobile security tools across various platforms and operating systems, and the evolving nature of cyber threats necessitating constant updates and upgrades. Furthermore, concerns regarding data privacy and compliance regulations are also influencing the adoption rate of certain security solutions. Competition is fierce, with established players like Palo Alto Networks, Check Point, and Trend Micro vying for market share alongside emerging players offering innovative and specialized solutions. The ongoing evolution of mobile technology and the continuous emergence of new threats require vendors to consistently innovate and adapt their offerings to maintain a competitive edge. The market will continue to see consolidation and partnerships as companies look to expand their reach and provide comprehensive mobile security solutions.
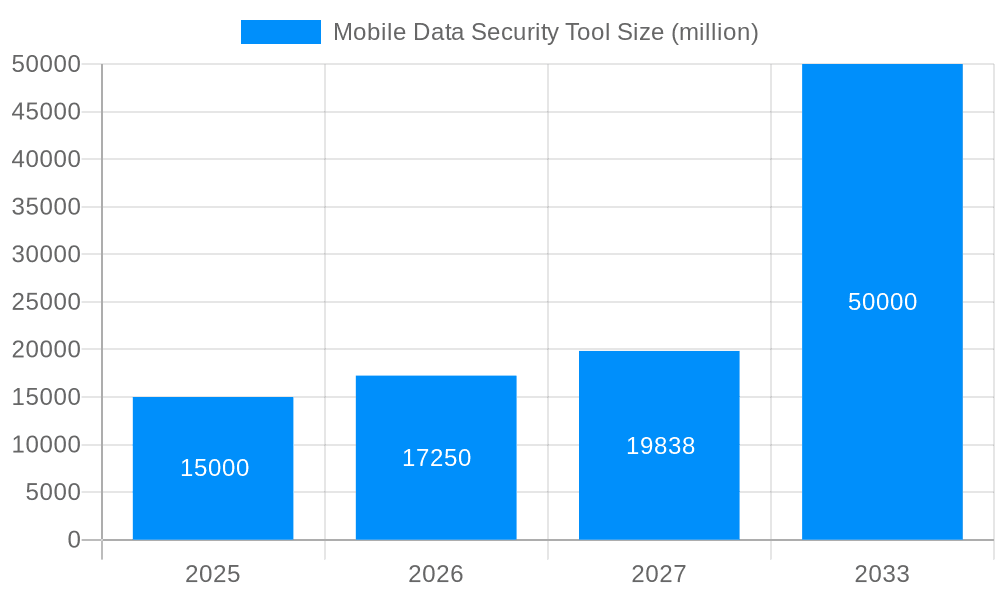

The global mobile data security tool market is experiencing explosive growth, projected to reach multi-billion dollar valuations by 2033. The study period from 2019 to 2033 reveals a consistent upward trajectory, with the base year of 2025 already demonstrating significant market maturity. The estimated market value for 2025 showcases substantial investment and adoption across various sectors. This expansion is fueled by a confluence of factors, including the escalating reliance on mobile devices for both personal and professional use, the increasing sophistication of cyber threats targeting mobile platforms, and the growing regulatory landscape demanding robust data protection measures. The forecast period (2025-2033) anticipates continued strong growth, driven by technological advancements such as improved AI-powered threat detection, enhanced encryption protocols, and the emergence of innovative security-as-a-service (SaaS) solutions. Analysis of the historical period (2019-2024) highlights a clear shift from primarily on-premises solutions towards cloud-based models, reflecting a broader industry trend toward agility and scalability. This trend is further emphasized by the rising adoption of mobile data security tools among both SMEs and large enterprises, signifying the universal recognition of the need for robust mobile security irrespective of organizational size. The market is witnessing a surge in the integration of mobile security tools into existing IT infrastructures, demonstrating a proactive approach to risk management across various industries. Furthermore, a notable trend involves the increasing collaboration between security vendors and mobile device manufacturers, creating more seamless and integrated security solutions.
Several key factors are driving the phenomenal growth of the mobile data security tool market. The ever-increasing reliance on mobile devices for business operations is a primary driver. Employees are increasingly accessing sensitive corporate data through smartphones and tablets, making mobile security a critical aspect of overall IT security strategy. The rising frequency and sophistication of mobile-specific cyber threats, including malware, phishing attacks, and data breaches, necessitate robust security solutions. Data privacy regulations, such as GDPR and CCPA, impose stringent requirements on organizations regarding the protection of personal data, fueling the demand for compliance-ready mobile security tools. The increasing adoption of cloud-based services and BYOD (Bring Your Own Device) policies further complicates the security landscape, requiring more comprehensive and flexible security solutions. The evolution of mobile technology itself, with new features and functionalities, constantly introduces new security vulnerabilities, requiring continuous adaptation and improvement of mobile security tools. This is complemented by the growing adoption of IoT (Internet of Things) devices, many of which are mobile, further expanding the attack surface and increasing the demand for effective security measures. Finally, the continuous innovation in mobile security technologies, like AI-powered threat detection and advanced encryption, is attracting more users and pushing growth in the sector.
Despite the significant growth potential, several challenges and restraints hinder the market's expansion. The complexity of mobile operating systems and the diversity of mobile devices present significant challenges for developing universal security solutions. Ensuring compatibility across different platforms and versions requires extensive testing and continuous updates, adding cost and complexity. The constant emergence of new mobile threats necessitates continuous improvement and adaptation of security tools, leading to ongoing maintenance and upgrade costs. Moreover, the balance between robust security and user experience remains a crucial challenge. Overly restrictive security measures can hinder productivity and user satisfaction, impacting adoption rates. The rising cost of implementing and maintaining mobile security solutions can be a significant barrier, particularly for SMEs with limited budgets. Another challenge lies in integrating mobile security solutions with existing enterprise security infrastructure. Effective integration requires careful planning and execution and necessitates skilled personnel capable of managing this complex technology. Finally, the limited awareness and understanding of mobile security threats among users can lead to careless practices, compromising the effectiveness of security tools.
The Large Enterprises segment is projected to dominate the mobile data security tool market during the forecast period (2025-2033). This dominance is due to several factors:
Higher Budgets: Large enterprises possess significantly larger IT budgets than SMEs, enabling them to invest in more advanced and comprehensive security solutions. They can afford the premium pricing associated with sophisticated mobile security tools offering advanced functionalities such as endpoint detection and response (EDR), data loss prevention (DLP), and mobile threat detection (MTD).
Greater Data Sensitivity: Large enterprises typically handle far more sensitive data than SMEs, including financial information, customer data, and intellectual property. The potential consequences of a data breach are far greater for larger organizations, driving them to prioritize robust mobile security measures.
Stringent Regulatory Compliance: Large enterprises often face more stringent regulatory compliance requirements related to data privacy and security. Meeting these regulations requires investing in security solutions that meet the highest standards and ensure compliance with relevant laws and regulations.
Complex IT Infrastructure: Large enterprises have significantly more complex IT infrastructure than SMEs. Integrating mobile security into a larger ecosystem requires specialized expertise and often involves working with multiple vendors, adding cost but also providing more robust protection.
Increased Cyber Threat Surface: Large enterprises often have a much larger number of mobile devices connected to their network, increasing their exposure to cyber threats. This larger surface makes targeted attacks more likely, emphasizing the need for advanced tools to manage threats.
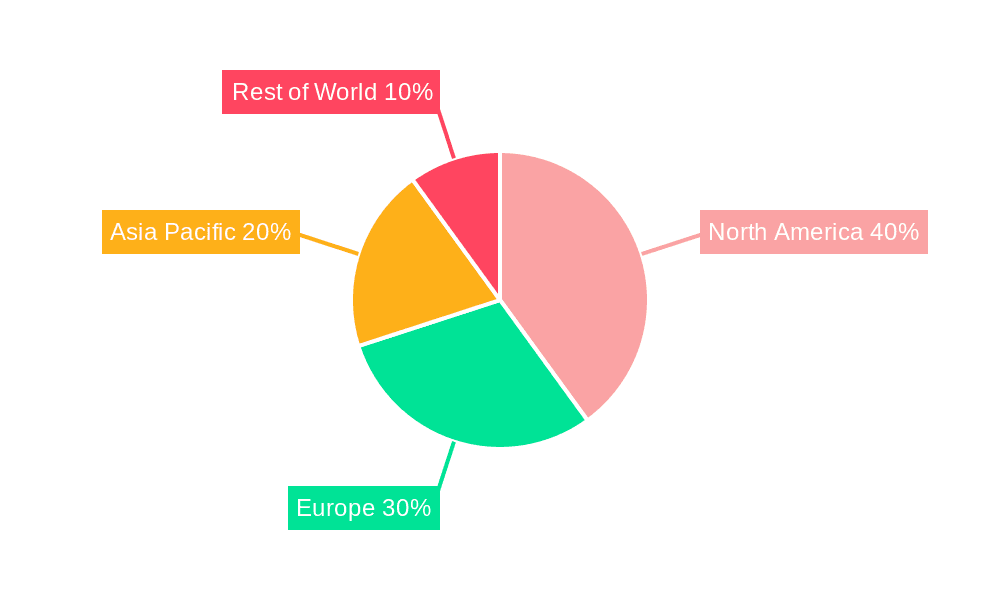
In terms of geographic regions, North America and Western Europe are expected to maintain significant market share due to high levels of technological adoption, strong regulatory frameworks supporting data protection, and a high concentration of large enterprises. However, the Asia-Pacific region is experiencing rapid growth, driven by the increasing adoption of smartphones and mobile technology across a diverse user base.
The mobile data security tool industry is experiencing a surge in growth, primarily fueled by the rising adoption of cloud-based solutions, increasing awareness of mobile security threats, stringent data privacy regulations, and the ongoing innovation in mobile security technologies, particularly in AI-powered solutions. These factors collectively contribute to a rapidly expanding market, creating opportunities for new entrants and sustained growth for established players.
This report provides a comprehensive overview of the mobile data security tool market, analyzing its current state, future trends, and key players. It delves into market drivers, challenges, and growth catalysts, offering a detailed understanding of market dynamics and opportunities for stakeholders across the value chain. The report's in-depth segment analysis and regional outlook offer actionable insights for investors, vendors, and end-users seeking to navigate this rapidly evolving landscape. A detailed competitive analysis helps understand the strategies adopted by key players.

| Aspects | Details |
|---|---|
| Study Period | 2020-2034 |
| Base Year | 2025 |
| Estimated Year | 2026 |
| Forecast Period | 2026-2034 |
| Historical Period | 2020-2025 |
| Growth Rate | CAGR of XX% from 2020-2034 |
| Segmentation |
|




Note*: In applicable scenarios
Primary Research
Secondary Research

Involves using different sources of information in order to increase the validity of a study
These sources are likely to be stakeholders in a program - participants, other researchers, program staff, other community members, and so on.
Then we put all data in single framework & apply various statistical tools to find out the dynamic on the market.
During the analysis stage, feedback from the stakeholder groups would be compared to determine areas of agreement as well as areas of divergence
The projected CAGR is approximately XX%.
Key companies in the market include Palo Alto, Check Point, ESET, Amazon, PreEmptive, Broadcom Inc, LIAPP, Prey, Salesforce, Trend Micro, zANTI, NetAlly, Dell Credant, SyncDog, Certo, Escrypt, WinMagic, BlueFletch, HiddenApp, Ribbon, Vera Security, OneSpan, Blackberry, Corrata, Guardsquare, SolarWinds, .
The market segments include Type, Application.
The market size is estimated to be USD XXX million as of 2022.
N/A
N/A
N/A
N/A
Pricing options include single-user, multi-user, and enterprise licenses priced at USD 4480.00, USD 6720.00, and USD 8960.00 respectively.
The market size is provided in terms of value, measured in million.
Yes, the market keyword associated with the report is "Mobile Data Security Tool," which aids in identifying and referencing the specific market segment covered.
The pricing options vary based on user requirements and access needs. Individual users may opt for single-user licenses, while businesses requiring broader access may choose multi-user or enterprise licenses for cost-effective access to the report.
While the report offers comprehensive insights, it's advisable to review the specific contents or supplementary materials provided to ascertain if additional resources or data are available.
To stay informed about further developments, trends, and reports in the Mobile Data Security Tool, consider subscribing to industry newsletters, following relevant companies and organizations, or regularly checking reputable industry news sources and publications.