1. What is the projected Compound Annual Growth Rate (CAGR) of the Cybersecurity?
The projected CAGR is approximately 9.3%.
MR Forecast provides premium market intelligence on deep technologies that can cause a high level of disruption in the market within the next few years. When it comes to doing market viability analyses for technologies at very early phases of development, MR Forecast is second to none. What sets us apart is our set of market estimates based on secondary research data, which in turn gets validated through primary research by key companies in the target market and other stakeholders. It only covers technologies pertaining to Healthcare, IT, big data analysis, block chain technology, Artificial Intelligence (AI), Machine Learning (ML), Internet of Things (IoT), Energy & Power, Automobile, Agriculture, Electronics, Chemical & Materials, Machinery & Equipment's, Consumer Goods, and many others at MR Forecast. Market: The market section introduces the industry to readers, including an overview, business dynamics, competitive benchmarking, and firms' profiles. This enables readers to make decisions on market entry, expansion, and exit in certain nations, regions, or worldwide. Application: We give painstaking attention to the study of every product and technology, along with its use case and user categories, under our research solutions. From here on, the process delivers accurate market estimates and forecasts apart from the best and most meaningful insights.
Products generically come under this phrase and may imply any number of goods, components, materials, technology, or any combination thereof. Any business that wants to push an innovative agenda needs data on product definitions, pricing analysis, benchmarking and roadmaps on technology, demand analysis, and patents. Our research papers contain all that and much more in a depth that makes them incredibly actionable. Products broadly encompass a wide range of goods, components, materials, technologies, or any combination thereof. For businesses aiming to advance an innovative agenda, access to comprehensive data on product definitions, pricing analysis, benchmarking, technological roadmaps, demand analysis, and patents is essential. Our research papers provide in-depth insights into these areas and more, equipping organizations with actionable information that can drive strategic decision-making and enhance competitive positioning in the market.
 Cybersecurity
CybersecurityCybersecurity by Type (Hardware, Software, Service), by Application (BFSI, IT & Telecom, Retail, Healthcare, Government, Manufacturing, Energy, Others), by North America (United States, Canada, Mexico), by South America (Brazil, Argentina, Rest of South America), by Europe (United Kingdom, Germany, France, Italy, Spain, Russia, Benelux, Nordics, Rest of Europe), by Middle East & Africa (Turkey, Israel, GCC, North Africa, South Africa, Rest of Middle East & Africa), by Asia Pacific (China, India, Japan, South Korea, ASEAN, Oceania, Rest of Asia Pacific) Forecast 2026-2034
The global cybersecurity market, valued at $140.58 billion in 2025, is projected to experience robust growth, driven by the increasing sophistication of cyber threats and the rising adoption of digital technologies across various sectors. A Compound Annual Growth Rate (CAGR) of 9.3% from 2025 to 2033 indicates a significant expansion, reaching an estimated market size of approximately $300 billion by 2033. Key drivers include the growing prevalence of ransomware attacks, data breaches, and the increasing reliance on cloud computing and Internet of Things (IoT) devices, which expand the attack surface. Furthermore, stringent government regulations mandating data protection and cybersecurity measures are compelling organizations across sectors like BFSI (Banking, Financial Services, and Insurance), IT & Telecom, Retail, Healthcare, and Government to invest heavily in cybersecurity solutions. The market is segmented into hardware, software, and services, with software solutions showing particularly strong growth due to the rising demand for advanced threat detection and response capabilities. Geographic growth will vary; North America and Europe currently hold the largest market shares, but the Asia-Pacific region is projected to witness the fastest growth due to increasing digitalization and government initiatives.
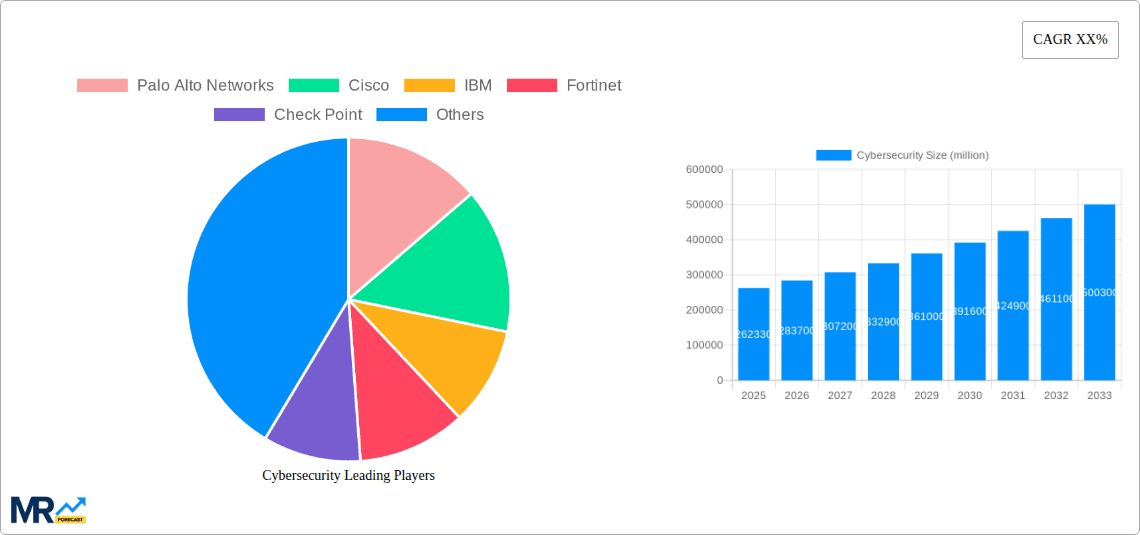

The competitive landscape is highly fragmented, with major players like Palo Alto Networks, Cisco, IBM, and Fortinet dominating the market. However, several smaller, specialized companies are also gaining traction, providing innovative solutions catering to niche requirements. Ongoing trends include the rise of Artificial Intelligence (AI) and Machine Learning (ML) in cybersecurity, the increasing adoption of cloud-based security solutions, and a greater focus on proactive threat detection and incident response. While growth is expected, restraints such as the skills gap in cybersecurity professionals and the evolving nature of cyber threats present challenges. The market's success hinges on the ability of companies to adapt to these evolving threats and provide effective, scalable solutions for a rapidly expanding digital ecosystem.
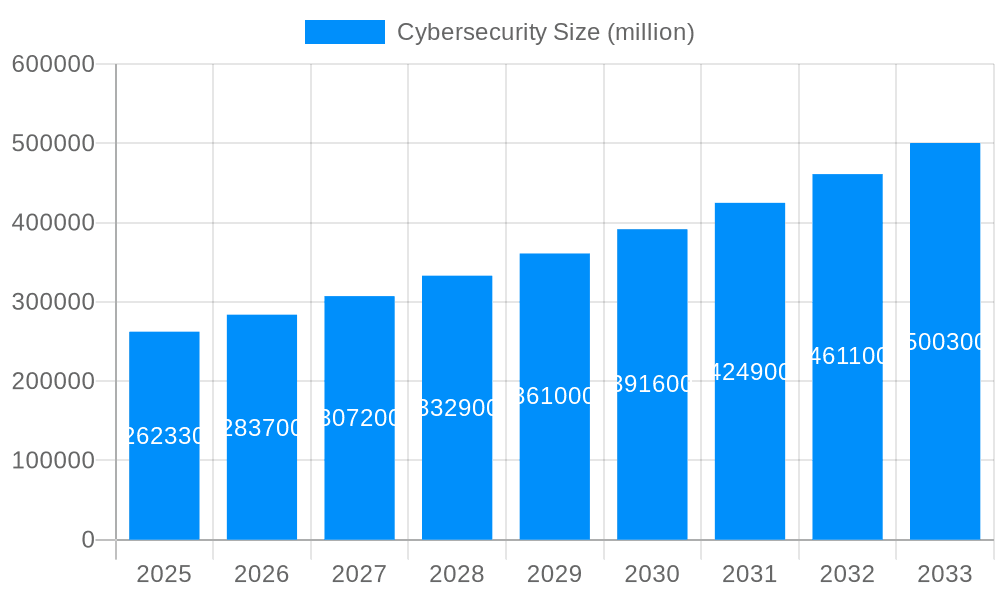

The global cybersecurity market is experiencing explosive growth, projected to reach hundreds of billions of dollars by 2033. From 2019 to 2024 (historical period), the market witnessed significant expansion driven by the increasing digitization of businesses and the rising sophistication of cyber threats. The estimated market value in 2025 is already in the tens of billions, signifying a robust and sustained growth trajectory. This growth is fueled by several converging factors: the escalating frequency and severity of cyberattacks targeting diverse sectors, the increasing reliance on cloud computing and IoT devices (expanding the attack surface), and the ever-evolving nature of cyber threats requiring continuous adaptation and investment in security solutions. The forecast period (2025-2033) anticipates continued expansion, driven by the adoption of advanced security technologies like AI-powered threat detection, blockchain for secure data management, and zero trust security architectures. Furthermore, stringent government regulations and increased awareness among businesses about the financial and reputational risks associated with data breaches are propelling investment in cybersecurity. Market segmentation reveals strong growth across various areas, with software solutions, cloud-based services, and security for critical infrastructure sectors like BFSI and healthcare exhibiting particularly high growth rates. Key players are constantly innovating, creating new product offerings, forming strategic partnerships, and engaging in mergers and acquisitions to consolidate market share and cater to the rising demand for comprehensive cybersecurity solutions. The overall trend indicates an increasingly complex and dynamic market characterized by continuous innovation, strategic partnerships, and an ever-increasing demand for robust and adaptable security measures. This necessitates continuous monitoring of emerging threats and proactive adaptation by both businesses and individuals. The study period (2019-2033) paints a picture of sustained and substantial market growth, underscoring the importance of cybersecurity in the modern digital landscape. The projected market size in the billions of dollars by 2033 reflects the significant economic and strategic importance of this sector.
The cybersecurity market's rapid expansion is driven by a confluence of factors. The increasing interconnectedness of devices through the Internet of Things (IoT) creates a vastly expanded attack surface, making organizations more vulnerable. Cloud adoption, while offering numerous advantages, also introduces new security challenges, demanding robust cloud security solutions. The rise of sophisticated cyberattacks, including ransomware, phishing, and advanced persistent threats (APTs), necessitates advanced security technologies and skilled professionals to counter them. Governments worldwide are implementing stricter data privacy regulations, such as GDPR and CCPA, forcing organizations to invest heavily in compliance measures. The high cost of data breaches, including financial losses, legal penalties, and reputational damage, is a significant driver, compelling businesses to prioritize cybersecurity investments. The increasing sophistication of cybercriminals demands continuous innovation in security technologies and strategies. Furthermore, the growth of e-commerce and the increasing reliance on digital transactions have expanded the potential targets for cyberattacks, further fueling market growth. This combined pressure necessitates proactive security measures, driving demand for a wider range of cybersecurity solutions across various industries. The need for robust cybersecurity infrastructure is no longer a luxury; it is an essential requirement for operating in the modern digital world.
Despite the burgeoning market, several challenges and restraints hinder the growth of the cybersecurity industry. The skills gap in cybersecurity is a major concern, with a shortage of qualified professionals capable of managing and mitigating complex threats. This shortage drives up the cost of skilled labor and can delay implementation of critical security measures. The complexity of cybersecurity solutions can be daunting for smaller organizations lacking the resources to manage and maintain sophisticated systems. Integrating diverse security solutions from multiple vendors can also be a significant challenge. The ever-evolving nature of cyber threats requires constant updates and adaptations, placing a strain on resources and budgets. The cost of cybersecurity solutions can be prohibitive for some businesses, particularly smaller enterprises, potentially leading to inadequate protection. Finally, the increasing reliance on artificial intelligence (AI) in both offensive and defensive cybersecurity strategies presents a unique challenge, as AI-driven attacks can be more sophisticated and difficult to detect. Overcoming these challenges requires a multi-faceted approach including investment in cybersecurity education and training, the development of user-friendly and cost-effective solutions, and the fostering of collaboration and information sharing amongst stakeholders.
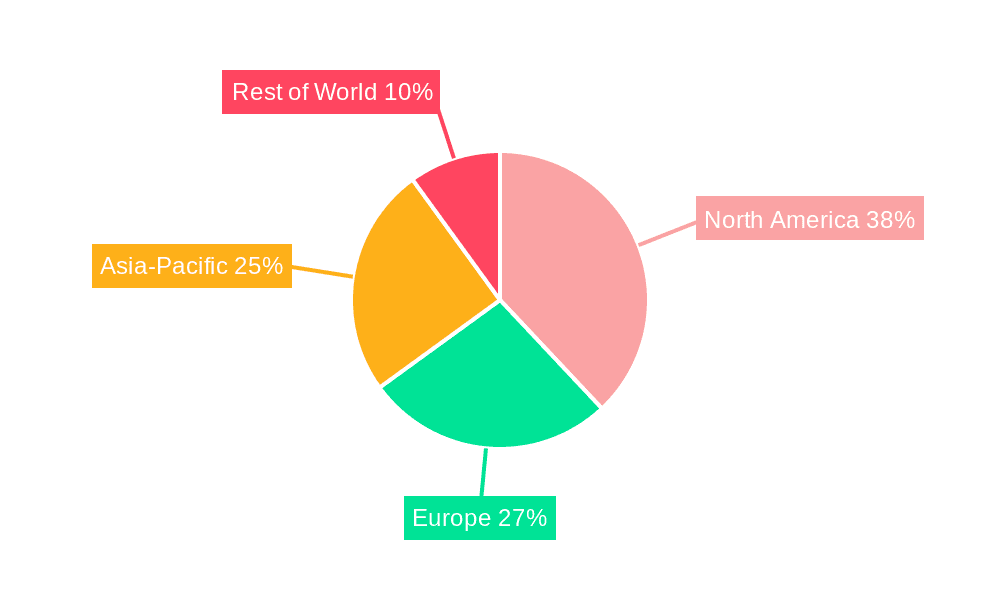
The North American region is expected to dominate the cybersecurity market throughout the forecast period (2025-2033) due to the high concentration of technology companies, substantial investments in R&D, and the early adoption of advanced security technologies. Europe is also expected to witness significant growth, driven by stringent data privacy regulations like GDPR. Asia-Pacific is expected to experience the fastest growth rate owing to increasing digitalization and rising government initiatives promoting cybersecurity. Within market segments:
Software: This segment is projected to hold the largest market share, driven by the growing demand for advanced security software solutions like endpoint detection and response (EDR), security information and event management (SIEM), and cloud access security brokers (CASB).
BFSI (Banking, Financial Services, and Insurance): This sector is a primary target for cyberattacks, leading to high investment in cybersecurity solutions to protect sensitive financial data and maintain customer trust. The high value of assets and stringent regulatory compliance requirements fuel the growth within this segment.
IT & Telecom: This sector is crucial for digital infrastructure, making it a prime target for cybercriminals. The need to protect sensitive customer data and critical network infrastructure drives significant investment in cybersecurity, contributing to substantial segment growth.
Reasons for Dominance:
The cybersecurity industry's growth is being significantly accelerated by the increasing sophistication of cyberattacks, the expanding attack surface created by IoT devices and cloud computing, stricter government regulations regarding data privacy and security, and the escalating cost of data breaches for organizations. These factors create a compelling environment for sustained investment and innovation within the cybersecurity sector. The rising adoption of artificial intelligence (AI) and machine learning (ML) in cybersecurity solutions further contributes to this growth.
This report provides a detailed analysis of the global cybersecurity market, encompassing market size, growth drivers, challenges, key players, and future trends. It offers valuable insights into the various market segments, regional dynamics, and emerging technologies shaping the cybersecurity landscape. This analysis provides businesses and investors with a comprehensive understanding of the opportunities and challenges in this rapidly evolving sector.

| Aspects | Details |
|---|---|
| Study Period | 2020-2034 |
| Base Year | 2025 |
| Estimated Year | 2026 |
| Forecast Period | 2026-2034 |
| Historical Period | 2020-2025 |
| Growth Rate | CAGR of 9.3% from 2020-2034 |
| Segmentation |
|




Note*: In applicable scenarios
Primary Research
Secondary Research

Involves using different sources of information in order to increase the validity of a study
These sources are likely to be stakeholders in a program - participants, other researchers, program staff, other community members, and so on.
Then we put all data in single framework & apply various statistical tools to find out the dynamic on the market.
During the analysis stage, feedback from the stakeholder groups would be compared to determine areas of agreement as well as areas of divergence
The projected CAGR is approximately 9.3%.
Key companies in the market include Palo Alto Networks, Cisco, IBM, Fortinet, Check Point, McAfee, Trend Micro, Broadcom (Symantec), RSA Security, QI-ANXIN, Venustech, Sangfor Technologies, CyberArk, TOPSEC, Rapid7, NSFOCUS, DAS-security, Asiainfo Security, Hillstone Networks, Dptech, .
The market segments include Type, Application.
The market size is estimated to be USD 140580 million as of 2022.
N/A
N/A
N/A
N/A
Pricing options include single-user, multi-user, and enterprise licenses priced at USD 3480.00, USD 5220.00, and USD 6960.00 respectively.
The market size is provided in terms of value, measured in million.
Yes, the market keyword associated with the report is "Cybersecurity," which aids in identifying and referencing the specific market segment covered.
The pricing options vary based on user requirements and access needs. Individual users may opt for single-user licenses, while businesses requiring broader access may choose multi-user or enterprise licenses for cost-effective access to the report.
While the report offers comprehensive insights, it's advisable to review the specific contents or supplementary materials provided to ascertain if additional resources or data are available.
To stay informed about further developments, trends, and reports in the Cybersecurity, consider subscribing to industry newsletters, following relevant companies and organizations, or regularly checking reputable industry news sources and publications.